It’s no surprise that WordPress powers 43% of the web. Since it’s open source, people from around the world are constantly contributing to improvements. Plus, because of its huge library of free and premium plugins, it’s pretty simple for someone with limited development knowledge to build a fairly complex site.
Latest news about Types of Malware and all other security threats can be found at Panda Security website which provides and present Collective Intelligence Monitor about all threats, as they said: ” The best way to defeat your enemy is to understand him.”
But, like with anything, WordPress site owners need to be constantly vigilant of cyber criminals who seek to take advantage of security gaps. And one of the biggest threats is malware.
That’s why learning how to remove malware from WordPress sites is so important. When you can identify when your WordPress site is infected, you can act quickly to clean it and prevent it from happening again in the future.
In this post, we’ll discuss the importance of detecting and removing malware on your WordPress site. Then we’ll walk you through how to do so — with and without a plugin. We’ll provide tips for protecting your site against malware in the future and then wrap up with some Frequently Asked Questions (FAQs).
One of the biggest horrors a site owner can experience is having their site hacked. This causes delays in the business and exposes information (both yours and your customers’) that can be used for various malicious acts. And even after you regain control of your site, you will lose the trust of affected customers. So being hacked is genuinely horrifying.
With that in mind, it is vital to know WordPress site vulnerabilities. Your knowledge of these vulnerabilities gives you the upper hand. Here are 9 of the most common WordPress site vulnerabilities and how you can address them:
Out of Date WordPress Version
Like everything around you, vulnerabilities evolve. To keep up, software developers ensure they stay one step ahead to protect their patrons. WordPress does just that. All the updates that are provided should not be taken for granted because these include improvements not only in functionality but also in security. Don’t make the mistake of not updating your WordPress version. Doing that will expose you to risks you would not want to experience.
SQL Injection
SQL injection refers to a technique used by hackers to infiltrate your site by injecting malicious codes into your site’s SQL statements. It can enable them to access your database, exposing all stored information.
To prevent SQL injection, you should control user input and how this affects your queries. Make sure your codes are written while keeping your database protected.
Cross-Site Scripting (XSS)
Another technique hackers use is cross-site scripting or XSS, which is the injection of malicious scripts, usually through a web application. The lack of user input validation is also the main culprit to this kind of attack. There are many types of XSS attacks, causing varying levels of consequences which range from pure disturbance to a full-scale account takeover.
Knowing this, you should take the validation of user input very seriously. Being too lax in this area exposes you to this threat and a lot more. Implement stricter rules in your programming, and ensure that anything that your users would key in is validated before being accepted.
Low-End Host Provider
Your choice of hosting provider plays an important role not only on your site’s performance but also in other aspects such as your site’s security. Since hosting entails costs, many websites, especially those running on a tight budget, end up availing the services of cheap providers. But, of course, a provider’s costs justify the quality of services it can give its users, so a low-end provider will have to make compromises to operate at low costs. Sometimes, this compromise is on security.
As a responsible site owner, you should always be serious about security. If you are starting with your site, make sure that you weigh your options. Never put security on second priority when you evaluate your shortlist. But if you already have a host running your site, assess if the security level is acceptable, and when it’s not, negotiate for fortifying your site’s security. This may lead to increased costs, but again, security is vital.
Weak Login Credentials
One of the most common mistakes of website owners is also a common mistake that most people commit: opting for weak login credentials. Simple credentials are very easy to remember, but such is also easy to guess, giving hackers the ability to steer the command of your site out of your hands.
To prevent your site from being hijacked, make sure that your admin user account, as well as its password, is hard enough to be a challenge to guess. Never settle for the default admin user account; do not use very obvious passwords.
Installing Untrusted Plugins of Your WordPress Site
A great thing about WordPress is the abundance of countless plugins that can help your site function to your satisfaction and that of your users. Unfortunately, while there are a lot of plugins that can be trusted, there are also some that are not. Going for untrusted plugins exposes you to risks that can put your site and your users in danger.
It is therefore advisable to only make use of trusted plugins. Make sure to scrutinize a plugin before you install it. Furthermore, ensure that you diligently update your plugins as hackers can even target plugins to gain access to your site.
Theme-related Vulnerabilities
Similar to plugins, there is also a wide range of themes that you can use for your WordPress site. However, themes also carry the same risks, so make sure you use the same scrutiny level when choosing the theme you would implement for your site. It is always best to be a bit of a cynic than to fall victim to hackers’ tricks.
Not Monitoring Your Logs
Your site activities are recorded, allowing you to review what has happened for a specific time. This also gives you the power to detect any strange activity. A lot, however, fail to utilize this power, especially those that have not experienced a hack firsthand.
Fortunately, your site has not been hacked yet but don’t be lax. Make sure to spend the effort in monitoring your logs so that you will be able to foil a possible hack.
Malware Vulnerabilities on your Computer
Finally, the computer for which you administer your site may also pose threats to your WordPress site. This is especially true in the case of malware that may be present on your computer. Protect both your computer and your WordPress site by employing reliable anti-malware tools.
The importance of malware detection and removal
Malware is a piece of software designed to harm or damage a computer system. It can come in the form of a virus, worm, Trojan horse, or spyware. Despite some strong security measures, WordPress sites are vulnerable to malware attacks.
There are many different ways that malware can get onto your WordPress site. The most common method is through malicious plugins or themes. Other ways include vulnerabilities in the core WordPress software or other software on your server.
Once the malware has infected a WordPress site, the person behind the attack can do a lot of damage — delete files, inject spammy links into your content, and even steal sensitive information like passwords and credit card numbers. Not only can this attack lead to unnecessary downtime, it can also hurt your reputation and lead to loss of business.
Without some sort of malware scanning tool, you may not immediately notice when your site has been infected. And the longer malware goes undetected, the more damage it can do. This is where the best WordPress security plugins come into play. They can detect and eliminate threats before serious damage occurs.
Identify threats with a free plugin
If you’re looking for a high-quality, free tool that monitors your site for you, Jetpack Protect is an excellent solution. It scans your site automatically for more than 28,700 vulnerabilities and provides recommendations for securing your WordPress site.
There are no complicated settings or confusing terminology. You can just turn it on, then rest easy knowing that you’ll be alerted the second that malware or vulnerabilities are found.
This is a great option for small businesses and new websites that want to better secure their WordPress site. Keep in mind, however, that the sole focus of Jetpack Protect is malware and threat identification, not removal. Keep reading for ways to remove malware from your WordPress site.
How to conduct WordPress malware removal with a plugin
The easiest and quickest way to detect and remove malware from WordPress sites is to use a plugin. Fortunately, there are a handful of options to choose from.
We recommend Jetpack Scan, which automates the entire process of WordPress malware removal, saving you significant amounts of time and energy. Plus, it’s super easy to set up on your website. It can be purchased on its own, but works best as part of Jetpack’s wider WordPress Security plan that provides comprehensive coverage. Note that it takes the functionality included with Jetpack Protect one step further, with one-click malware fixes.
Step 1: Scan your WordPress site for malware
First, if you haven’t already, you’ll need to install the Jetpack plugin and purchase Jetpack Scan. Once the tool is activated, you can scan your WordPress site for malware.
To do so, navigate to Jetpack and click on the Scan button.
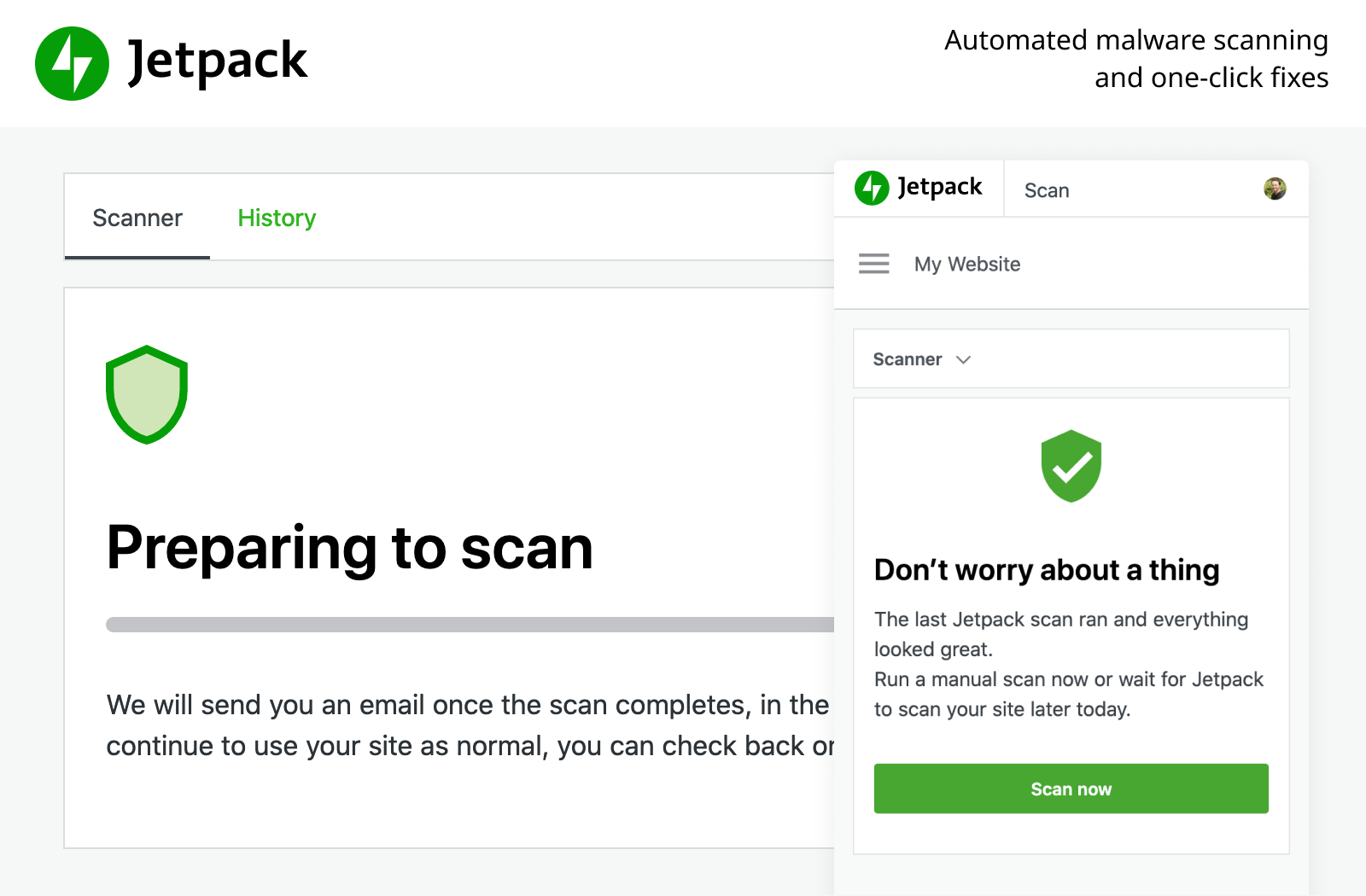
Jetpack will now scan your site for any known malware threats. This process will likely take just a couple of minutes.
Step 2: Clean up detected malware (with 1 click)
Ideally, no malware is detected, and your scan returns a “No vulnerabilities found” result.

But if any malware is found, you’ll see a list of issues under Malware Threats Found. To remove the malware, simply click on the Remove threat button next to each one.
That’s all there is to it! The plugin will automatically clean malware from WordPress for you. Again, this process will take just a few minutes at most.
Step 3: Remove malware warnings from your WordPress site
If Google has detected malware on your website, it will likely display a warning to prevent visitors from trying to access it. This is a major problem because most potential visitors won’t proceed past this message.
So, once you’ve identified and cleaned malicious code from your site, the last step is to remove these warnings. If your site has been flagged, you can file a review request with Google. Then it’s just a matter of waiting for a response.
It’s really important that you don’t miss this step. See our full guide on how to remove your WordPress site from Google’s blocklist.
How to conduct WordPress malware removal without a plugin
Although it’s usually faster (and easier), you don’t have to use a plugin to remove malware. There are some instances where a plugin may not be able to remove the threat, and in that case, it’s definitely a good idea to know the manual approach.
It’s important to note that this approach involves a number of steps and requires a decent amount of time. It’s almost always better to use a malware removal plugin, if you can.
Step 1: Put your WordPress site into maintenance mode
The first thing you’ll need to do is put your site into maintenance mode. This process hides your website content from visitors and shows a message telling them that your site will return soon.
You can put your site into maintenance mode using a plugin like WP Maintenance Mode & Coming Soon.
This free tool lets you easily enable maintenance mode on your site in just a few clicks. After you install and activate it, you can navigate to Settings → WP Maintenance Mode.

Next, select Activated as the Status. When you’re done, click on the Save settings button at the bottom of the screen. Your site will now go into maintenance mode.
Step 2: Create a full backup of your WordPress site and database
Having a backup of your WordPress site is always a good idea. It can help you recover your site if something goes wrong or you accidentally delete something.
There are two aspects you’ll need to back up: your database and your files. The database is where your content, settings, and user information are stored. Your files are everything else, like your themes, plugins, and images.
The best way to do this is with a WordPress backup plugin like Jetpack Backup. Not only does it provide an easy way to download your files and database on demand, it also automatically backs up your site in real-time. So, in the future, every single one of your changes will be saved.
However, you can back up your WordPress site manually, using File Transfer Protocol (FTP) tools and phpMyAdmin. This method is just more technical and time-consuming.
Step 3: Identify all malware on your site
Once you’ve prepped your site, the next step is identifying any malware. This involves searching your database, files, and source code.
One way to do this is to use a malware scanner tool like Malwarebytes.
If you’re looking to identify malware manually, you’ll need to go through each of the key areas of your site to look for signs of infection. In your database, you can search for common syntaxes often used by cybercriminals (you can refer to Step 9 for some popular examples of malicious PHP).
If you’re scanning your source code for malware, there are two main types of attributes to look for: script and iframe. Lines that start with “script=>” or “iframe src=URL>” and contain suspicious URLs or file names are common red flags.
Step 4: Replace all WordPress core files with a clean installation
If you have a corrupted WordPress installation, one of the best ways to clean your hacked site is to replace all of the core WordPress files with a fresh set. When doing this, you’ll only keep your original wp-config.php file and wp-content folder.
First, download a fresh copy of WordPress from WordPress.org.
Unzip the file, then delete the wp-config.php file and wp-content folder. These are the only two folders you should delete — everything else should be left intact.
Next, you can use your File Manager or FTP client to upload the remaining files to your server. This step will overwrite your existing installation. Learn how to bulk upload files via FTP.
Step 5: Remove any malicious code from the wp-config.php file
It’s also a smart idea to compare your wp-config.php file to the original offered by the WordPress Codex. This step will make it easier to identify and locate anything that has been added (like malicious code).
From the WordPress Codex, download a fresh copy of the wp-config.php file. Open the file as well as your existing wp-config.php file in a text editor to compare them. There are some legitimate reasons your file may be different from the original — especially when it comes to information about your database — but take the time to look for anything suspicious and remove it if necessary. When you’re done, save the cleaned-up file, then upload it to your server.
Step 6: Re-install a clean version of your theme
Next, you’ll want to re-install a clean version of your WordPress theme. But if you’re using a child theme (a copy of your theme with the functions and styling of its parent, plus custom edits), you don’t want to lose all of your work. Therefore, you’ll need to reinstall a clean version of your theme while keeping your child theme intact.
From your WordPress dashboard, navigate to Appearance →Themes, then deactivate your parent theme. Next, go to your File Manager or FTP and delete your parent theme folder.

If you’re using a theme from the WordPress repository, head there, search for your theme, then download the latest version. If you’re using a premium theme, or a free option from elsewhere, you’ll need to download your theme files from that source. From your dashboard, navigate to Appearance →Themes, then select Add New → Upload Theme.

Select the zipped file you just downloaded. After uploading it, click on the Activate button.
Now you can activate your child theme. Your site should now be running the latest version of the parent theme, with all your customizations from the child theme intact.
Step 7: Check for recently-modified code files and repair them
The next step is to look at any files that have been recently modified. To do this manually, you can connect to your site via FTP or File Manager, then sort your files based on the last modified date column:

Make a note of any files that have recently been changed. Then go through each of them to review the code for suspicious additions. These could include PHP functions such as str_rot13, gzuncompress, or eval.
Step 8: Clean hacked database tables
If your WordPress site has been infected with malware, there’s a chance that it created malicious content in your database tables.
To clean your tables, log in to your phpMyAdmin dashboard — available through your hosting provider — then navigate to the database table that has been infected with malicious content to remove it. You can determine which tables have been affected using a scanner tool (like Jetpack) or by comparing the original files to your current ones.
Note that you should create a backup of your site first, and you can find the original files in previous backups. You can then look for commonly-used functions (see the next step), suspicious links, etc. If you locate any, you can manually delete that content.
Save your changes, then test your website to verify that it’s still working correctly. If you don’t want to modify your database tables manually, you can also use a tool like WP-Optimize.
While it’s not a malware removal plugin, it can clean and optimize your database. But, if you want to use a plugin to detect and clean WordPress malware, we recommend a dedicated solution like Jetpack Scan.
Step 9: Identify and remove hidden backdoors
When hackers gain entry into your site, they’ll often leave behind a hidden ‘backdoor’ (a way to get back in). This entry area is usually embedded into files that are similarly named to your regular WordPress files, only placed in the wrong directory locations.
To identify and remove hidden backdoors from your WordPress site, you’ll need to search popular files and folders, including wp-content/plugins, wp-content/uploads, and wp-content/themes.
When checking these files, there are a variety of PHP functions to look for, including:
exec
system
assert
base64
str_rot13
gzuncompress
eval
stripslashes
preg_replace (with /e/)
Move_uploaded_file
These functions don’t inherently indicate malicious activity. But the manner and context in which they’re used can sometimes indicate and introduce risks.
For example, malicious PHP usually:
- Is located immediately before or after valid code, so that it can run undetected.
- Contains long strings of random characters (letters and/or numbers).
- Was recently inserted into your code.
- Contains reinfectors (malware that duplicates if you delete it) like 444 permissions or fake plugin folders.
As with database tables, we recommend comparing your existing files to the originals to determine whether there’s a legitimate reason for the code to be there.
Note that editing WordPress files can break key functions of your site, so it’s best to only do this if you have experience working with them. Otherwise, we recommend using a plugin like Jetpack Scan or hiring a professional.
How to protect your WordPress site from future malware attacks
Learning how to remove malware from WordPress sites is incredibly useful. But it’s better to know how to prevent malware from infecting your website in the first place. Let’s discuss some actions you can take!
1. Change your WordPress password and database credentials
One of the most important things you can do to prevent malware attacks on your WordPress site is to change your password and database credentials regularly. Doing this can make it much more difficult for hackers to access your site.
To change your password, log in to your WordPress dashb,oard and go to Users → Profile.
From here, you can scroll to the Account Management section and select Set New Password.

When you’re done, click on Update Profile at the bottom of the screen. Once you’ve changed your password, be sure to log out of all active sessions on your website. These include any devices or browsers you may have used to access your WordPress site.
You should also regularly change your WordPress database credentials. To do this, you’ll need to edit your wp-config.php file. This file is located in the root directory of your WordPress installation and can be accessed via FTP or File Manager.
Once you’ve opened wp-config.php, look for the following lines:
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'database_name_here' );
/** MySQL database username */
define( 'DB_USER', 'username_here' );
/** MySQL database password */
define( 'DB_PASSWORD', 'password_here' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );You’ll want to update the DB_NAME, DB_USER, and DB_PASSWORD values with new ones. Once you’ve done that, save and close the file.
For these values to work, you’ll also have to update them on your server so that they match. To do this, you can log in to your phpMyAdmin account and navigate to your database. Next, open the users table and select Edit.

You can update the credentials as necessary. When you’re done, click on the Go button.
2. Regularly update your WordPress site, themes, and plugins
Outdated software is one of the most common ways hackers gain access to WordPress sites. Therefore, another way to prevent malware attacks is to keep your website updated. This step helps ensure your site has the latest security features and patches.
To update WordPress core, log in to your dashboard and click on Updates. If there’s a new version of WordPress available, you’ll see a notice at the top of the screen.

You can click on the Update button to install the latest version.
Updating your plugins and themes is just as important as updating WordPress itself. Most plugin and theme developers release security updates regularly.
You can do this by logging in to your WordPress site and checking the Updates tab. You’ll see any available plugin or theme updates under the main WordPress version updates.
Then, select the Update Plugins or Update Themes button to install the latest versions. If you want to automate this process, you can also use the Jetpack’s Automatic Plugin Updates feature. It will automatically install new versions of WordPress, plugins, and themes as soon as they’re released.
You’ll need to install and activate the Jetpack plugin to enable this feature. Once you connect it to your WordPress.com account, you can navigate to Jetpack → Settings → Writing.
Next, scroll to the Automated Updates section at the bottom of the page, then select which types of updates you want to enable: WordPress Core Updates, Plugin Updates, and/or Theme Updates.
When you’re done, remember to save your changes. You can also manage updates on your Activity Log page. You can select the Update All button to run them all at once.
3. Install an automated malware scan plugin for WordPress
You should also regularly scan your WordPress site for malware using a plugin like Jetpack Scan. Jetpack Scan will review your site for known malware and send you an email if they find anything wrong.
Once you download and install the plugin on your site, you can access the malware scan tool by clicking on Jetpack → Backup & Scan in the WordPress dashboard. There, you can see the current status of your site, and run a new scan if you’d like.
4. Install an automated backup plugin for WordPress
To prevent malware attacks and practice good overall security for your WordPress site, we suggest installing an automated backup plugin like Jetpack Backup.
Jetpack Backup is the best WordPress backup plugin because it saves your website in real-time. If anything changes — a page is updated, a post is published, a product is purchased, etc. — the latest backup file will reflect that. Plus, it integrates seamlessly with Jetpack Scan.
So, if malware is found on your site, you’ll get a notification from Scan letting you know. Then, you can immediately restore a backup from right before the hack happened — even from your mobile device, if you’re on the go! — and skip all the complicated malware removal steps above.
WordPress malware removal FAQs
At this point, hopefully, you have a solid understanding of how WordPress malware detection and removal work. To ensure we covered the key areas, let’s wrap up with some FAQs!
What are the signs of a WordPress malware infection?
There are several signs that your WordPress site has been infected with malware. First, you may notice your site loading slowly or displaying error messages.
Second, you may see new users or files appearing on your site that you didn’t add. Finally, you may find that your website is on Google’s blocklist or is being blocked by visitors’ antivirus software.
If you see any of these signs, it’s important to take action immediately to clean up your WordPress site. Ignoring a malware infection can lead to severe consequences, including data loss and website downtime.
How does malware generally infect a WordPress site?
There are a few different ways that malware can infect a WordPress site. First, it can come in through a WordPress plugin or theme vulnerability.
It can also be uploaded by a hacker who gains access to your site through an insecure password or other method.
Can I remove malware from WordPress myself?
You always have the option of hiring an outside firm to remove malware from your site, but it usually gets pretty expensive. Instead, you can identify and remove malware from WordPress using a plugin like Jetpack. This is a fast, easy, and reputable solution.
If you’re an experienced developer, yes, you can manually remove malware from WordPress. This is a tedious process that has the potential to cause major errors on your site. You should proceed with caution if you choose this option.
Strengthen the security of your WordPress site
WordPress is a flexible and powerful CMS, but because it’s so popular, hackers will sometimes target sites that use it. One of the most significant risks facing WordPress websites is malware.
As we discussed in this post, there are multiple methods to detect and remove malware in WordPress. The easiest and fastest solution is to use a plugin like Jetpack. Alternatively, you can conduct malware removal manually. We also recommend regularly updating your WordPress software and creating backups to prevent issues in the future.
Looking for a hands-off, trusted way to automatically monitor your site for malware and vulnerabilities? Try the free Jetpack Protect plugin.
Do you want to take advantage of one-click malware removal and a library of additional security features? Get Jetpack Security today!
main blog source from here – https://jetpack.com/blog/wordpress-malware-removal/